How the ClickFix Malware Campaign Uses Fake CAPTCHAs to Spread Malware
Introduction
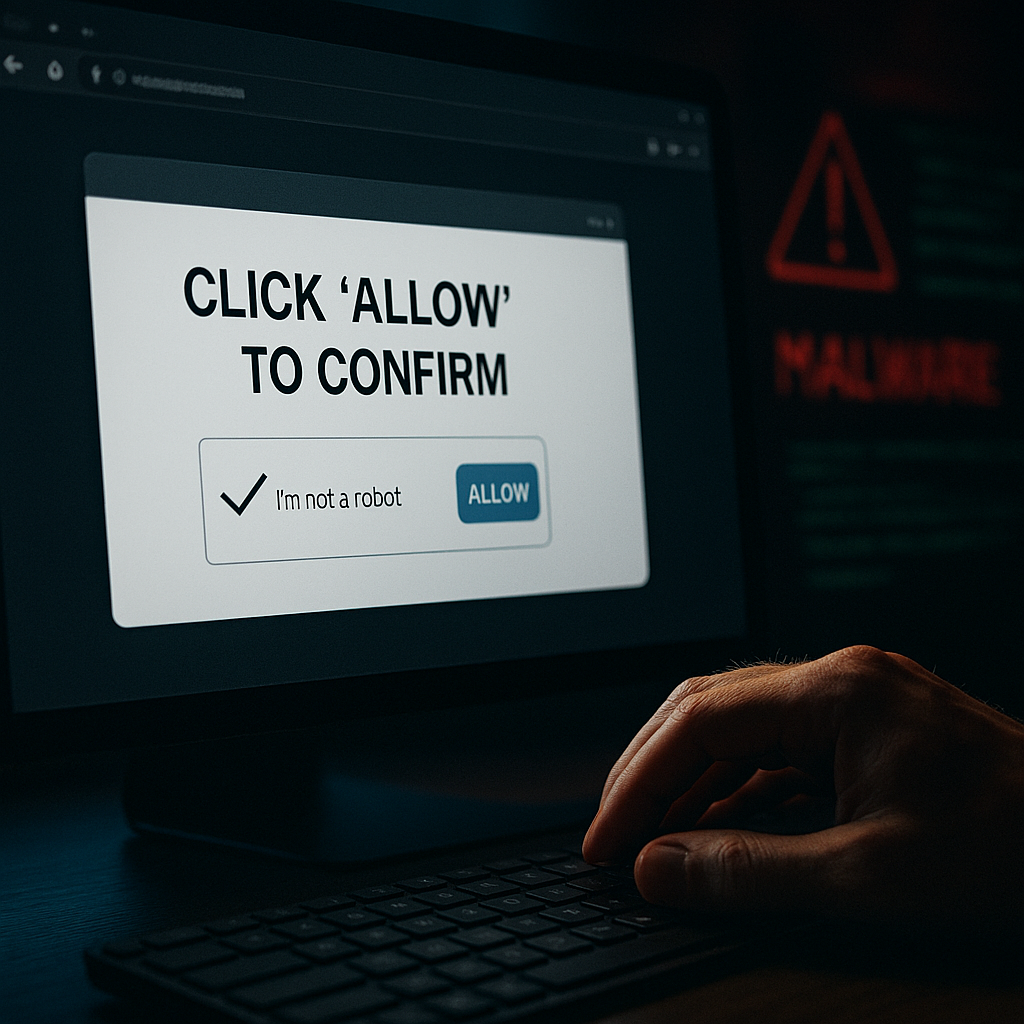
The ClickFix malware campaign first appeared in 2024. Since then, it has quickly become one of the top cyber threats of 2025. In fact, it now makes up nearly 8 percent of all blocked attacks—second only to phishing. Unlike most scams, ClickFix uses fake CAPTCHA messages to fool users. As a result, people unknowingly run harmful commands that infect their devices.
How the ClickFix Scam Works
- Fake prompts and trick messages
First, the attacker shows a fake CAPTCHA or error message. Then, the message asks the user to copy and paste a code into the Run box or terminal. When this happens, the victim launches a harmful script without knowing it. - Multiple steps in the attack
Next, the script contacts a server and downloads malware. This often includes tools like Lumma Stealer, RedLine, AsyncRAT, and NetSupport. These programs can steal passwords or give hackers full control of the system. - Works on many devices
Although it began on Windows, ClickFix now targets macOS, Linux, Android, and iOS. On phones, the malware can even install itself when someone just visits a bad website. - Used by advanced hacker groups
In recent months, government-backed hacker groups have also started using ClickFix. These include teams from North Korea, Iran, and Russia. This shows how dangerous and popular the method has become.
Growing Threat in 2025
- Huge growth in attacks
Security reports show a 500 percent jump in ClickFix attacks from late 2024 to mid-2025. Clearly, it is now a major cyber threat. - Common tool for hackers
Because it works well and is easy to use, ClickFix has replaced older fake-update scams. Many cybercriminals prefer this method to spread their malware.
Why ClickFix Is So Effective
- It plays on human habits
Many people trust prompts that look real. When they see a CAPTCHA or error box, they assume it’s safe to follow the instructions. This is exactly what attackers rely on. - Fake websites look real
Hackers copy popular brands like Booking.com or Cloudflare. They also use tricks to make their fake sites rank high in search engines. This makes their scams seem more real. - Hard for software to catch
Since the user runs the command on their own, many antivirus programs don’t catch it. This makes the attack hard to stop.
How to Stay Safe
- Teach users what to avoid
Everyone should know not to copy and paste commands from unknown websites or pop-ups. - Watch for strange behavior
Security teams should track when system tools like PowerShell or mshta.exe are used in odd ways. - Block risky websites
Use tools that block bad links and stop people from visiting fake sites. - Always go to the real website
Instead of clicking links, users should type in known websites themselves. - Limit access and permissions
Make sure users can’t run powerful system tools unless it’s truly needed. This reduces the damage if something goes wrong.
Conclusion
The ClickFix malware campaign shows how social engineering still works well for attackers. Because it tricks users into acting, it’s hard for software alone to stop. As it spreads to more platforms and is used by more hacker groups, it’s critical to stay alert. By combining user training, better tools, and strict rules on what can run, organizations can protect themselves from this growing threat.



Comments are closed