Building a BYOD Policy for Clinics Handling PHI (with Template)
Personal phones and tablets are already in exam rooms, on rounding carts, and in staff pockets. The question for most clinics is not whether BYOD exists, but whether it is controlled well enough to protect PHI and hold up during a HIPAA review.
A solid BYOD policy does two things at once: it keeps patient data private, and it keeps clinical work moving. For Sacramento area clinics and specialty practices, that balance matters because small teams often need mobility, after-hours responsiveness, and secure messaging without adding complexity.
Why BYOD hits differently in healthcare
When a device creates, receives, maintains, or transmits ePHI, it falls into HIPAA Security Rule territory. Ownership does not change that. A personal iPhone used to review labs, message a provider, or snap a clinical photo is part of your risk surface.
This is where many clinics get stuck: they want convenience, but they also need enforceable safeguards, audit evidence, and a plan for what happens when a device disappears.
One sentence that belongs in every clinic’s BYOD policy: BYOD access is a privilege that can be removed at any time.
Common clinic scenarios that your policy should address
A policy that only talks about “phones” and “passwords” will fail in real workflows. Your staff will run into edge cases immediately, and they will make up their own rules under pressure.
After you map your workflows, it becomes easier to write requirements that staff can follow.
- Physician on call reviewing charts after hours
- MA texting a patient about an appointment time
- Nurse using a personal tablet to access the EHR through a mobile app
- Provider taking a wound photo for documentation
- Billing staff checking patient statements from home
Those scenarios each have different risk and different technical controls.
Decisions to make before you write the policy
You can draft a BYOD template quickly, but you should not publish it until you make a few operational decisions. These choices drive everything else: scope, tooling, and enforcement.
Most clinics start with a small set of allowed uses and expand only after controls are proven.
- Allowed device types
- Allowed roles (and explicitly excluded roles)
- Whether BYOD can ever store PHI locally
- Whether you will require MDM or a managed “work container”
- Whether access is allowed from outside the United States
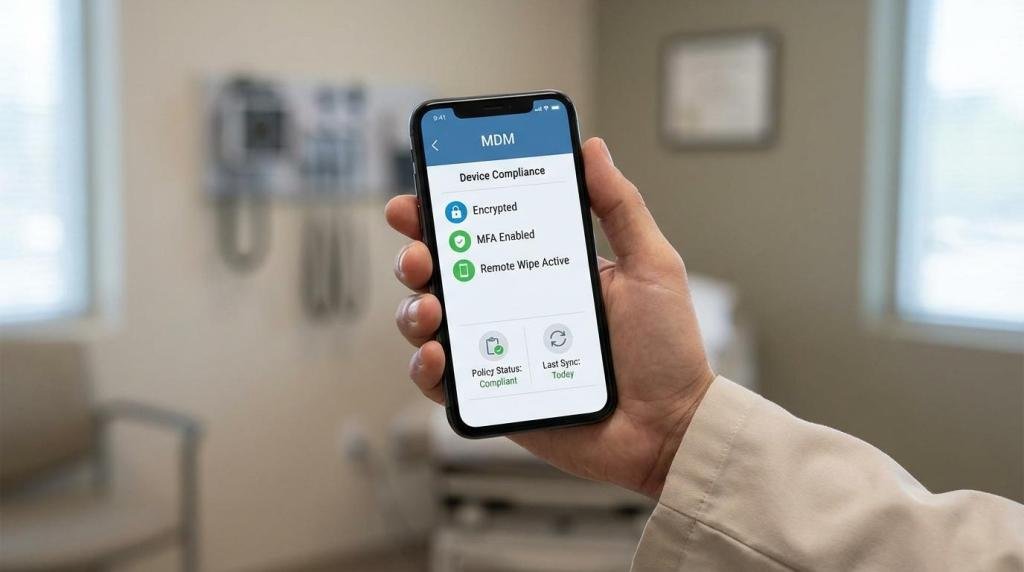
Required safeguards, mapped to what auditors expect
HIPAA does not give a single BYOD checklist, but it does expect administrative, physical, and technical safeguards that match your risks. For BYOD, that typically means you need to show you can control access, protect data at rest and in transit, and respond quickly when something goes wrong.
The table below is a practical way to align technical controls with the proof you will want in an audit or incident review.
| Control area | What “good” looks like in a BYOD program | Evidence to keep |
|---|---|---|
| Device enrollment | Every device is registered to a specific user before access is granted | Device inventory export, enrollment date, assigned user |
| Encryption | Device storage encryption enabled; encrypted connections to clinic systems | MDM compliance report, EHR access configuration |
| Authentication | Unique user IDs; MFA for EHR, email, VPN, and messaging | MFA policy, screenshots/config exports, access logs |
| Session protection | Auto-lock, short idle timeout, no shared accounts | MDM policy settings, HR attestation |
| App control | Only approved apps handle PHI; no copying PHI into personal apps | Approved app list, container policy, DLP settings if used |
| Remote response | Remote lock/wipe available and tested | Test records, incident tickets |
| Monitoring | Access logs reviewed; alerts for risky sign-ins | SIEM/SOC reports, periodic log review record |
| Training | BYOD-specific training and acknowledgements | Training roster, signed policy acknowledgements |
A Sacramento-based managed IT provider with a SOC can help clinics turn these items into ongoing monitoring and monthly compliance reporting, which is often the difference between “we have a policy” and “we can prove we enforce it.”
BYOD policy template for clinics handling PHI
Copy, paste, and edit the template below. It is written to be enforceable, not aspirational. Keep it in plain language, and route it through your compliance and HR process before rollout.
Document name: Bring Your Own Device (BYOD) Policy
Effective date: [DATE]
Owner: [HIPAA Security Officer / IT Manager]
Applies to: Workforce members, contractors, and trainees who access clinic systems on personal devices
Related policies: Acceptable Use, Access Control, Incident Response, Sanctions, Data Retention, Telehealth
1) Purpose
This policy establishes minimum requirements for the use of personally owned devices to access clinic systems and ePHI. The goal is to support patient care while protecting confidentiality, integrity, and availability of ePHI.
2) Definitions
- BYOD device: A personally owned smartphone, tablet, laptop, or other endpoint approved for clinic access.
- ePHI: Electronic protected health information as defined under HIPAA.
- MDM: Mobile Device Management or equivalent endpoint management platform approved by the clinic.
3) Scope and permitted use
Permitted device types: [Smartphones, tablets, laptops]
Not permitted: [Smartwatches/wearables, shared family devices, rooted/jailbroken devices]
Permitted user roles: [Physicians, NPs/PAs, nurses, clinical leadership, billing, scheduling]
Excluded roles: [Example: volunteers, visitors, any role without a documented job need]
Permitted activities on BYOD:
- Accessing the EHR using approved methods
- Secure messaging using an approved platform
- Approved telehealth platform use from a private environment
- Clinic email and calendar use if configured per this policy
Prohibited activities:
- Storing ePHI in personal email, notes, photos, or consumer cloud backups
- Transmitting PHI over SMS/MMS or consumer messaging apps
- Copying and pasting ePHI into non-approved apps
- Using public/shared computers to manage BYOD access
4) Device registration and ongoing compliance
All BYOD devices must be registered and approved before accessing clinic systems.
Users must complete the following before access is granted:
- Enrollment: Device enrolled in [MDM/endpoint manager] and assigned to the user
- Attestation: User signs BYOD acknowledgement and remote wipe consent
- Compliance check: IT verifies required settings are applied and reporting correctly
The clinic may block access automatically when a device falls out of compliance.
5) Minimum technical requirements (non-negotiable)
All BYOD devices approved for ePHI access must meet these minimum requirements:
- Supported OS version with automatic updates enabled
- Full-device encryption enabled
- Screen lock enabled with a strong passcode and biometric lock where supported
- Auto-lock after [X minutes] of inactivity
- MFA enabled for EHR, email, VPN, and approved messaging
- Remote lock and remote wipe capability enabled
- No jailbreaking/rooting; no disabled security protections
After you state requirements, make the acceptable use expectations explicit.
- Keep it separate: Use only clinic-approved apps and accounts for clinic work.
- Report fast: Lost, stolen, or suspected compromise must be reported immediately.
- Protect privacy in public: Do not view or discuss PHI where it can be overheard or seen.
6) Data handling rules (minimum necessary)
Workforce members may access only the minimum necessary ePHI required to perform job duties. ePHI must not be downloaded, exported, or stored locally unless explicitly approved in writing by [Security Officer] and secured in a managed container.
Clinical photos and videos are prohibited on the native camera app unless the clinic uses a controlled clinical media workflow that encrypts, uploads to the medical record, and removes local copies.
7) Network and remote access
- Clinic Wi-Fi access for BYOD must use the designated secure network.
- Remote access to clinic systems must use [VPN / secure access portal] with MFA.
- BYOD devices may not connect to clinic systems from jailbroken/rooted devices or from networks that interfere with encryption or device compliance checks.
8) Monitoring, privacy, and user consent
The clinic may monitor and log access to clinic systems from BYOD devices, including device identifiers, login activity, and access times. The clinic does not intend to access personal content, but security tooling may collect device compliance and security telemetry.
Users acknowledge that the clinic may remotely wipe clinic data, and if required for risk reduction, may wipe the entire device.
9) Incident reporting and response
Users must report any of the following immediately: lost/stolen device, suspected malware, suspicious prompts for passwords, accidental disclosure, or any situation where PHI may have been exposed.
Incident response steps should be short and executable.
- User notifies [Helpdesk phone] and [Security Officer contact] immediately.
- IT/Security initiates remote lock/wipe and disables active sessions as appropriate.
- Security documents the event, preserves logs, and performs breach risk assessment per clinic process.
- User completes follow-up steps, including password resets and device re-enrollment if allowed.
10) Enforcement and sanctions
Violations of this policy may result in loss of BYOD privileges, corrective action up to termination, and reporting as required by law and clinic policy. Devices that are out of compliance may be blocked without notice.
11) Review schedule
This policy is reviewed at least annually and whenever there is a material change in technology, workflows, or security risk.
Acknowledgement:
I have read and agree to comply with this BYOD policy. I understand the clinic may remove my access and may remotely wipe clinic data to protect patients and clinic operations.
Name: __________ Signature: __________ Date: __________
How to roll this out without disrupting care
Most BYOD programs fail because they are introduced as a one-time document instead of an operational process. Start small, prove enforcement, then expand.
A practical rollout sequence for clinics:
- Pilot with a limited group (example: providers only) for 30 to 60 days.
- Require enrollment before access and make that the only path, with no exceptions.
- Train on the “why” using real clinic scenarios: texting, photos, after-hours access, travel.
- Run a compliance report weekly at first, then move to monthly with spot checks.
- Test remote wipe on a few test devices and document the results.
In Sacramento and Elk Grove, clinics often find that the hardest part is not technical setup. It is consistency across roles, locations, and urgent workflows.
Where managed IT and SOC monitoring fit
A BYOD policy is a control. It still needs enforcement, telemetry, and quick response when a device is lost or a credential is phished. That is where managed IT and SOC-backed monitoring can support clinics: maintaining device inventory, watching sign-in anomalies, validating encryption and MFA coverage, and coordinating incident response documentation when time matters.
If you want, share your clinic size, EHR platform, and whether you want MDM-required BYOD or “no PHI stored locally” BYOD, and I can adapt the template language to match that operating model.