What is Network Segmentation? A Beginner’s Guide to a More Secure Network
In today’s digital landscape, security threats are everywhere—from phishing emails to ransomware attacks. One of the smartest ways to strengthen your organization’s cybersecurity is through network segmentation.
But what is network segmentation, and why is it so important?
What is Network Segmentation?
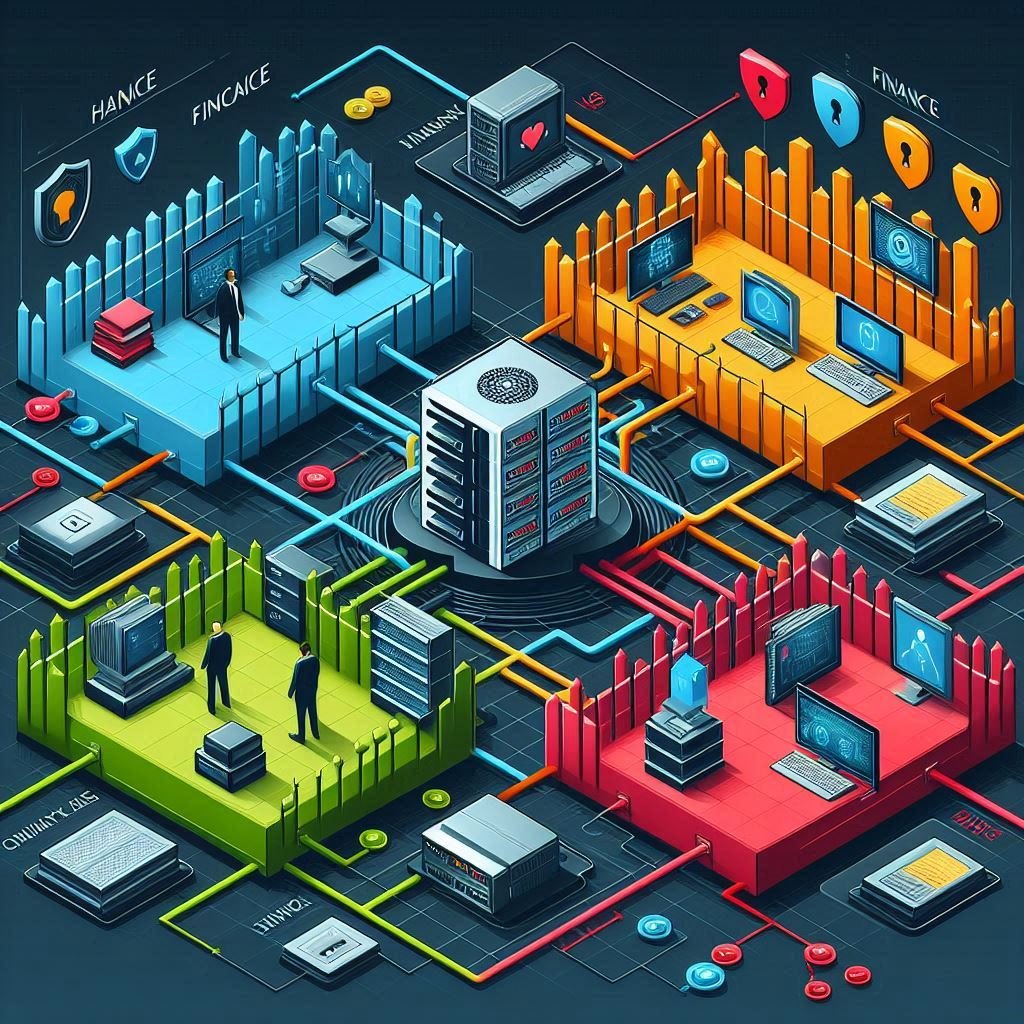
Network segmentation is the practice of dividing a computer network into smaller, isolated sections or “segments.” Each segment acts like a mini-network within your overall infrastructure.
This allows administrators to control and limit traffic between different parts of the network—reducing risk and improving security.
Why Segment a Network?
Here are some key reasons to segment your network:
1. Improved Security
If a hacker gains access to one segment, they can’t easily move laterally to others. This minimizes the damage in case of a breach.
2. Better Performance
Traffic within each segment stays localized. This reduces congestion and improves network performance and speed.
3. Simplified Compliance
Regulations like HIPAA, PCI-DSS, and GDPR often require data isolation and control. Segmentation helps you stay compliant more easily.
4. Enhanced Monitoring & Control
Admins can monitor traffic in specific segments and apply custom rules for access and behavior.
🛠️ Types of Network Segmentation
There are several ways to segment a network:
- Physical Segmentation: Using separate switches, routers, or firewalls.
- Virtual LANs (VLANs): Logical segmentation on a shared infrastructure.
- Firewall-Based Segmentation: Using firewalls to restrict communication between zones.
- Software-Defined Segmentation: Dynamic segmentation using software, often found in cloud environments.
Real-World Example
Imagine a company with three departments:
- HR
- IT
- Finance
If the network isn’t segmented, an employee in HR could (accidentally or maliciously) access sensitive financial data.
With segmentation, each department has its own isolated network, so HR can’t access Finance files unless explicitly allowed.
Best Practices for Network Segmentation
- Use the principle of least privilege.
- Segment based on function, risk level, or compliance needs.
- Regularly audit and update firewall and access rules.
- Implement intrusion detection and logging per segment.
Final Thoughts
Network segmentation isn’t just for large enterprises—it’s for any organization that values security, control, and efficiency. Think of it as building rooms inside your digital house. If a burglar breaks into one room, it doesn’t give them the keys to the whole building.
Whether you’re protecting sensitive customer data or just trying to keep your systems running smoothly, network segmentation is a smart, strategic step.


Comments are closed