The Importance of Regularly Reviewing Your Breach Response Plan
Table of contents
In today’s digital landscape, where cybersecurity threats are ever-present, businesses must prioritize the effectiveness of their breach response plans. Unfortunately, many organizations adopt a “set-it-and-forget-it” mentality, neglecting the need for regular updates and reviews. This oversight can lead to severe consequences during a security incident. In this article, we’ll explore why it’s critical to regularly review your breach response plan to ensure robust cybersecurity.
Why Regular Reviews of Your Breach Response Plan Are Essential
1. Adapting to an Evolving Threat Landscape
Cybercriminals continually develop new tactics, making it essential for businesses to adapt their cybersecurity measures. Regularly reviewing your breach response plan ensures that it addresses the latest threats effectively. Staying informed about current trends and threats is vital. Learn more about the evolving threat landscape.
2. Ensuring Compliance with Regulatory Requirements
Many industries face specific regulations regarding data protection and breach responses. These requirements change over time, and regular updates to your breach plan help ensure compliance, reducing the risk of legal penalties. For businesses operating in regulated sectors, compliance is critical. Check industry-specific compliance guidelines.
3. Integrating New Technologies
As technology evolves, so does your IT infrastructure. Regular reviews allow you to incorporate new technologies and tools into your breach response plan, ensuring you leverage advancements in cybersecurity. Adapting to technological changes is essential for maintaining a strong security posture. Explore the latest cybersecurity technologies.
4. Learning from Past Incidents
Every security breach provides valuable lessons. Conducting a review after an incident helps identify weaknesses in your breach plan and informs improvements for future readiness. Understanding past breaches enhances your organization’s resilience against similar threats. Read case studies on breach responses.
5. Strengthening Employee Training and Awareness
Cybersecurity is not just about technology; it’s about people too. Regularly updating your breach response plan ensures that all employees are trained and aware of their roles in the event of a breach. An informed workforce is crucial for preventing incidents and responding effectively. Find resources for employee cybersecurity training.
Key Components of an Effective Breach Response Plan
1. Identification and Assessment
Quick identification of a breach is crucial for effective response. Your plan should outline detailed steps for recognizing and assessing the severity of an incident. Efficient threat detection is the first line of defense in managing your breach. Learn about threat detection methods.
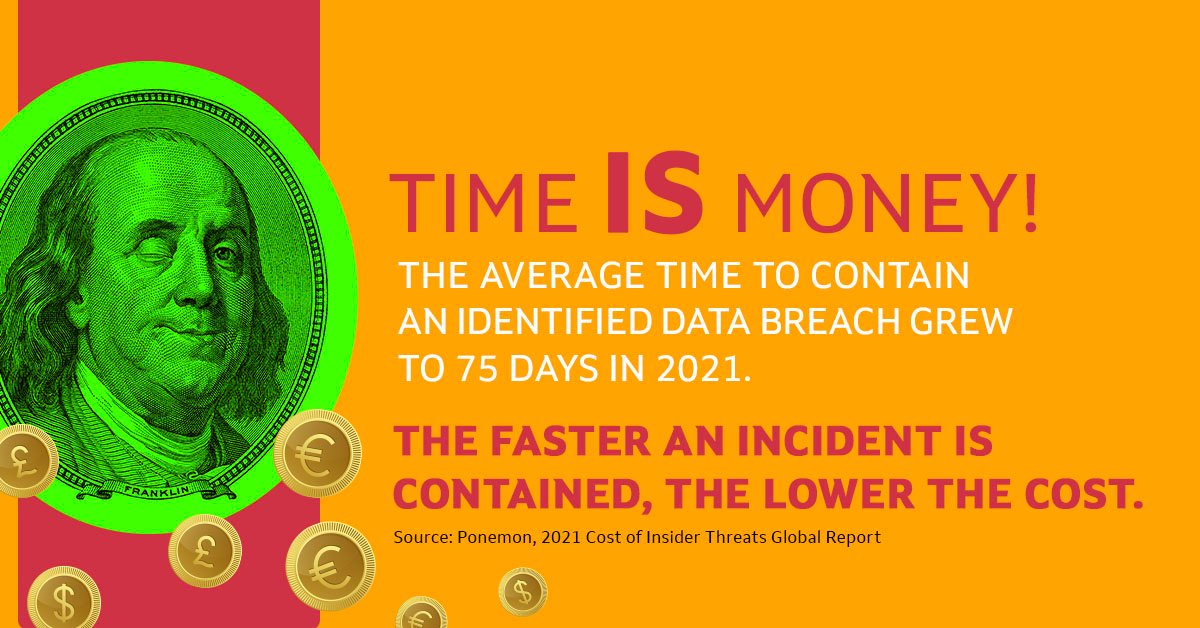
2. Containment and Eradication
Once a breach is confirmed, your team must know how to contain the incident and eliminate the threat. A well-defined containment strategy can minimize damage and facilitate a swift recovery. Incorporate your breach response plan into containment protocols. Discover strategies for incident containment.
3. Communication Strategy
A clear communication plan is essential during a cybersecurity incident. Your response plan should include procedures for notifying affected parties, informing stakeholders, and complying with regulatory requirements. Effective communication helps maintain trust with customers and partners during a breach. Read about best practices for incident communication.
4. Post-Incident Review
After resolving an incident, conduct a comprehensive review to analyze what happened, why it occurred, and how to prevent future incidents. Continuous improvement of your breach response plan is key to effective cybersecurity. Understand the importance of post-incident reviews.
5. Regular Testing and Drills
Routine drills and testing of your breach response plan ensure that your team is prepared to act swiftly and effectively during a real incident. Simulated scenarios help identify gaps in your plan and improve response times. Explore how to conduct effective cybersecurity drills.
Taking Action: Update Your Breach Response Plan Today
When was the last time your business reviewed its breach response plan? If it’s been a while, now is the time to take action. Don’t wait for a breach to expose vulnerabilities in your cybersecurity strategy.
Contact us today to learn how we can help you update your breach response plan and ensure your business is prepared for potential cyber threats. With proactive measures and a well-structured response plan, you can protect your organization from the damaging effects of cybersecurity incidents.
Conclusion
Regularly reviewing and updating your breach response plan is vital for fostering a culture of cybersecurity awareness within your organization. By understanding the importance of ongoing evaluation and improvement, you can significantly reduce the risks posed by cyber threats and protect your business’s reputation and assets.



Comments are closed