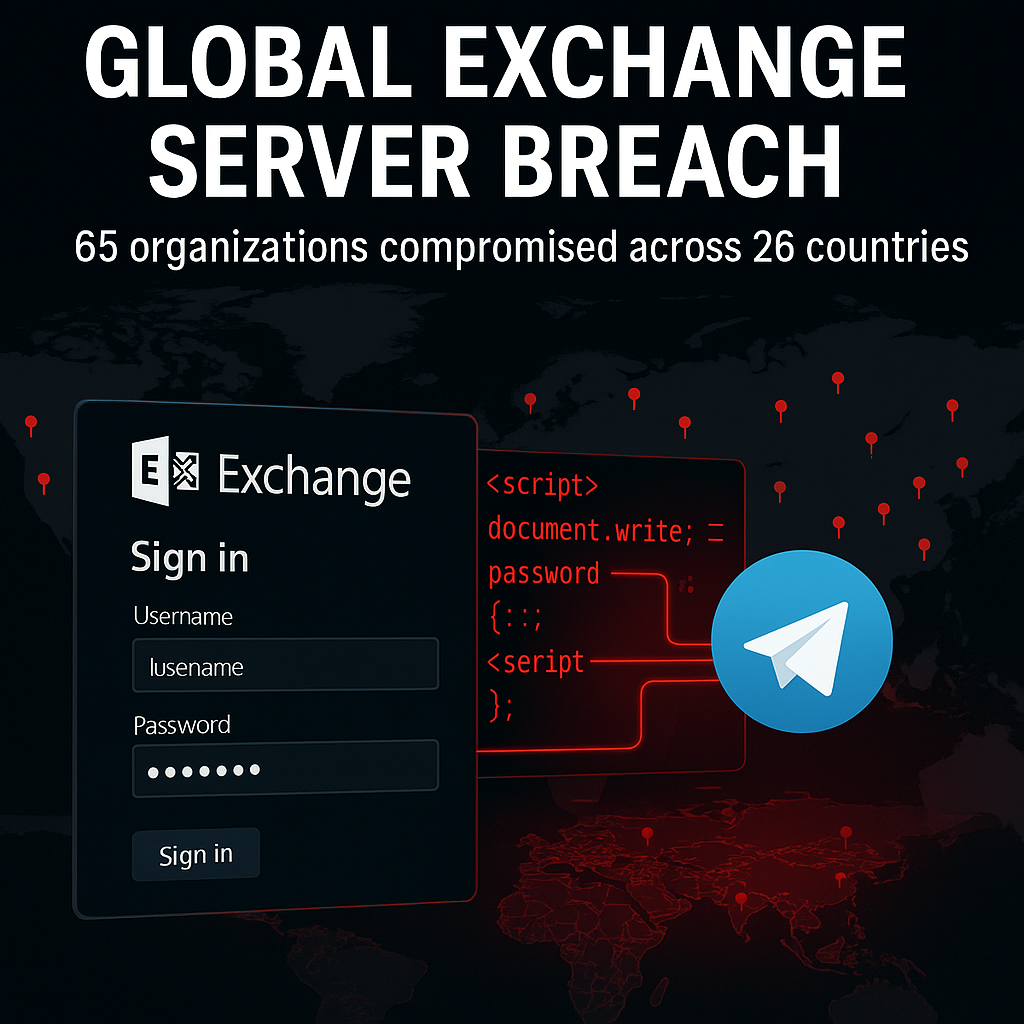
Microsoft Exchange Servers Breached: Keyloggers Target 65 Organizations Across the Globe
Hackers have compromised 65 Microsoft Exchange servers in 26 countries, embedding keyloggers into Outlook login pages. This Microsoft Exchange Server keylogger attack, identified by Positive Technologies, steals user credentials silently and efficiently.
Keyloggers Hide in Plain Sight
The attackers took advantage of servers exposed to the internet. By exploiting known Exchange vulnerabilities—including ProxyShell (CVE-2021-34473) and ProxyLogon (CVE-2021-26855)—they injected JavaScript keyloggers into login forms, further emphasizing the risk of a Microsoft Exchange Server keylogger attack.
Once active, the scripts either store credentials locally or send them directly to external servers and Telegram bots. In some cases, during a Microsoft Exchange Server keylogger attack, they also steal cookies, user agents, and timestamps.
A Broad and Alarming Reach
Affected entities range from government departments to industrial firms. Countries hit include Vietnam, Russia, Taiwan, China, Pakistan, Australia, and Turkey. The Microsoft Exchange Server keylogger attack scale shows just how widespread and organized the campaign is.
Moreover, this isn’t a one-time breach. The campaign has evolved from initial probes in 2024 to full-scale credential harvesting in 2025.
Detection and Mitigation Tactics
To spot these intrusions, security teams should:
- Scan OWA login pages for unknown JavaScript injections
- Check for new or unusual files, such as ‘websso.js’
- Monitor outgoing connections to Telegram or suspicious APIs
As a precaution, all exposed Exchange servers should be patched immediately. It’s also wise to install behavioral threat detection tools and audit login scripts regularly.
Why This Matters
Credential theft through silent keyloggers isn’t just a technical issue—it’s a gateway to long-term access and internal compromise. As attackers impersonate users, they can pivot through systems unnoticed, expanding their reach within the network.



Comments are closed