Cisco FMC RADIUS Vulnerability CVE-2025-20265: Patch Now to Prevent Remote Code Execution
Cisco has released emergency updates to fix a severe RADIUS authentication vulnerability in its Secure Firewall Management Center (FMC) Software. This flaw holds a CVSS score of 10.0, the highest possible rating. If attackers exploit it, they can run arbitrary shell commands with elevated privileges through network-based attacks. Because of its severity, security teams must act quickly.
Vulnerability Overview
- CVE Identifier: CVE-2025-20265
- Score: 10.0 (base score)
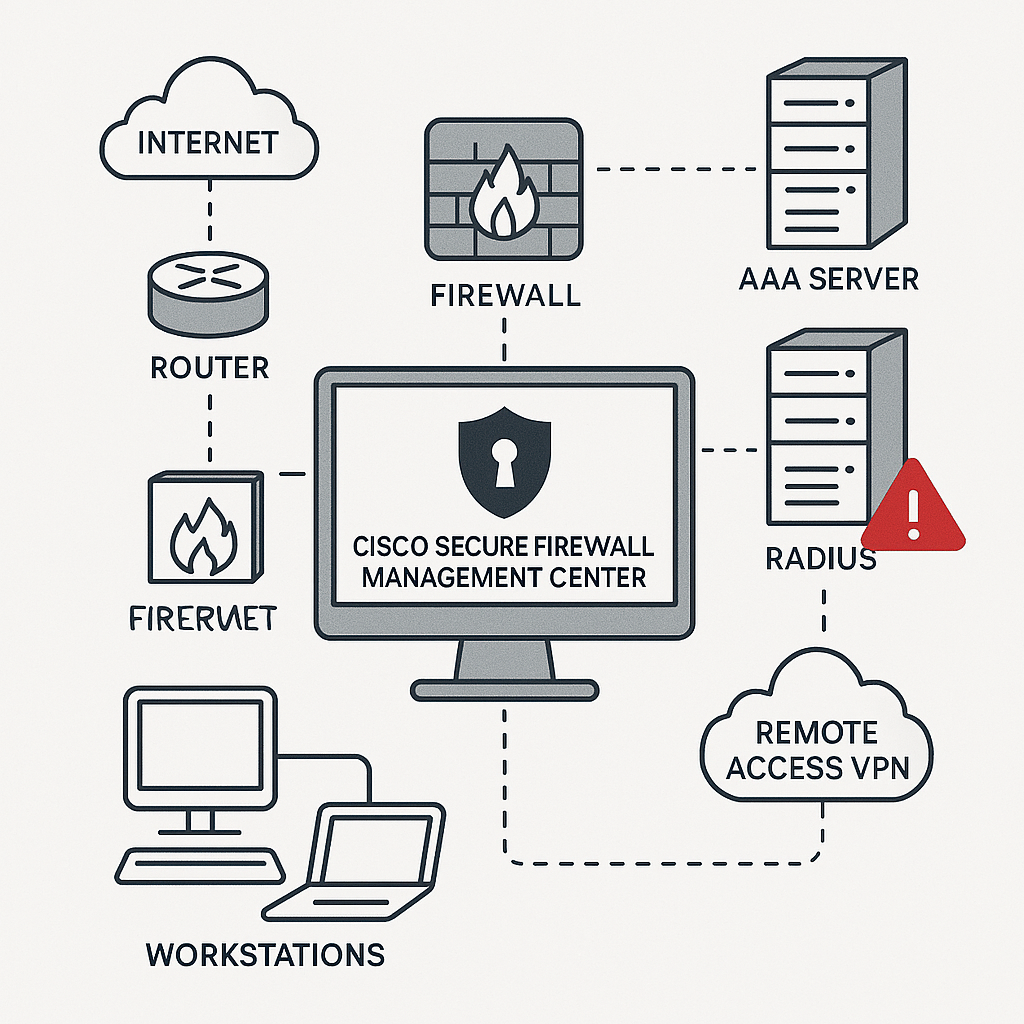
- Component: RADIUS subsystem of Cisco Secure FMC Software
- Cause: The RADIUS authentication process fails to handle certain inputs correctly. Attackers can exploit this weakness by sending crafted credentials, which trigger command execution.
Affected Versions & Conditions
Only certain versions face this risk. Systems running Cisco Secure FMC Software versions 7.0.7 and 7.7.0 become vulnerable if RADIUS authentication is active for the web interface, SSH management, or both. In contrast, Cisco Secure Firewall ASA and Threat Defense (FTD) products remain unaffected.
Exploitation Risk
Attackers do not need to log in before launching an attack. They can simply send malicious credentials that the RADIUS service processes, giving them full control at a high privilege level. Consequently, organizations that leave the flaw unpatched face a serious threat.
Mitigation & Remediation
To protect systems, security teams should take the following steps:
- Install the patch immediately: Cisco provides updates that remove the vulnerability in affected versions.
- Consider authentication changes: If patching cannot happen right away, disable RADIUS temporarily and use local accounts, LDAP, or SAML SSO instead.
- Harden the network: Restrict access to management interfaces using ACLs, segmentation, and strong firewall rules.
- Monitor systems closely: Review logs for suspicious activity and investigate unusual login attempts.
Since Cisco offers no temporary workaround beyond disabling RADIUS, installing the update remains the safest option.
Context & Urgency
This flaw appears in Cisco’s August 2025 Semiannual Firewall Advisory, alongside other security issues. Although no public reports confirm active exploitation yet, the vulnerability’s simplicity makes it attractive to attackers. By patching now, organizations can avoid becoming an easy target.
Recommended Action Plan
- Step 1: Identify all FMC systems using versions 7.0.7 or 7.7.0 with RADIUS enabled.
- Step 2: Download and apply Cisco’s security update without delay.
- Step 3: Disable RADIUS temporarily if updates cannot be applied immediately.
- Step 4: Isolate management interfaces from general network access.
- Step 5: Increase log monitoring frequency for early detection of threats.
Conclusion
CVE-2025-20265 represents a rare and critical security flaw in enterprise firewall management. Attackers can exploit it without logging in, giving them full control of the system. Organizations that use Cisco FMC with RADIUS should patch at once, strengthen access controls, and watch for any suspicious activity. Taking action today prevents major security breaches tomorrow.



Comments are closed